What a firewall Protects You From
|
There are times that you may want remote users to have access to items on your network. Some examples are: -Web server -SMTP server -FTP server In cases like this, you may want to create a DMZ (Demilitarized Zone).It is just an area that have less restrictions to be accessed from the external users. Many topologies are used to setup a DMZ area ,we choose 2 typical topologies : 1- Screened subnet topology 2- Multihomed topology (triple homed) Where, Each firewall can support one or more of the functions described below. -Static packet filters -stateful filtering or stateful inspection -A proxy is a software -Network Address Translation (NAT) 1- Screened subnet topology The most secure (and most expensive) option .In this case, the DMZ is placed between two firewalls from two different vendors,(for better security performance). 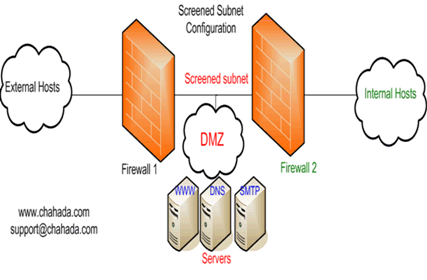 This solution allows organizations to offer services securely to Internet users.Any servers that host public services are placed in the Demilitarized Zone (DMZ),which is separated from both the Internet and the trusted network by the firewall. Therefore, if a malicious user does manage to compromise the firewall, he or she does not have access to the Intranet ( providing that the firewall is properly configured). 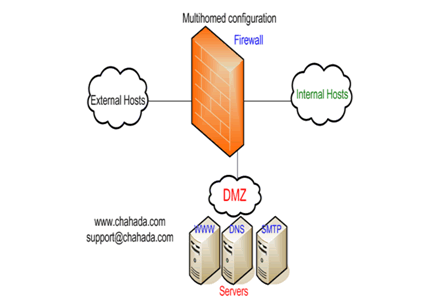 Resources:http://www.howstuffworks.com/firewall.htmhttp://www.more.net/technical/netserv/tcpip/firewalls/index.html http://www.infomusic.it/infomusic/Sic/FirewallProxy.aspx http://searchsecurity.techtarget.com |


